ICT Security Products - Crystal Security Product Family
- Full-line Information Security
- Intelligent IT Security Assessment System
- Crystal Security Keeper, CSK
- Cloud and Data Security
- Cloud-threat Intelligent Appliance, CIA
- Crystal Data Scanner, CDS
Crystal Information Security Total Solution
The Crystal Information Security Total Solution can strengthen a company's information security constitution, promptly fend off real-time web threats, perform full-scale monitoring of information security events, and rapidly analyze intrusive behavior by malicious software, defend companies' web application services and dramatically reduce the risk of information security events. The solutions include:
Crystal Security Keeper (CSK):
CSK is a solution to provide continuous monitoring based on security compliance. CSK leverages industry standards such as the SCAP (Security Content Automation Protocol) and OVAL (Open Vulnerability and Assessment Language) to assess and score the security configuration issues and vulnerabilities of machines. Enterprises can apply specified security baselines such as USGCB in CSK to monitor and maintain an effective security configuration settings.
Cloud-threat Intelligent Appliance (CIA):
CIA provides malicious analysis service for e-mail attachments.
Crystal Data Scanner (CDS):
CDS scans for confidential data stored on the endpoint including laptops, desktops, and workstations in order to inventory, secure, or relocate that data.
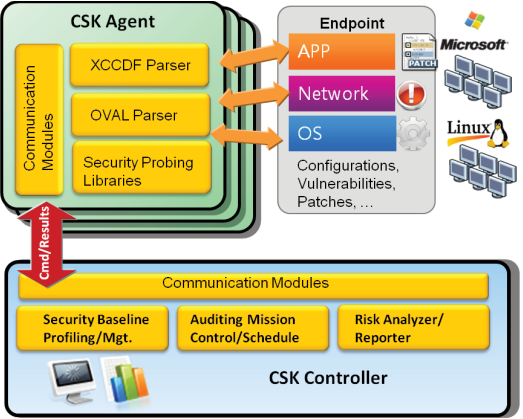
CSK software includes two major parts: CSK Controller –The security governance service platform, and CSK Agent –The information security endpoint auditing software.
- CSK Controller:
Functions of CSK Controller include information security baseline editing, assessment mission management, correlation analysis of assessing results and risk evaluation. The CSK Controller keeps baseline repository such as system configuration, software vulnerabilities, application patches and profiles. It associates with complex detection rules and standards, evaluating threats as well as managing assessing process. - CSK Agent:
CSK Agent is a piece of installation-free green software running as a service on endpoints, directly detecting configurations, vulnerabilities, software vulnerabilities and application patches. Based on security baselines specified by CSK Controller, it examines OS, network services and applications’ security status across endpoints as well as reports to CSK Controller for further risk analysis.
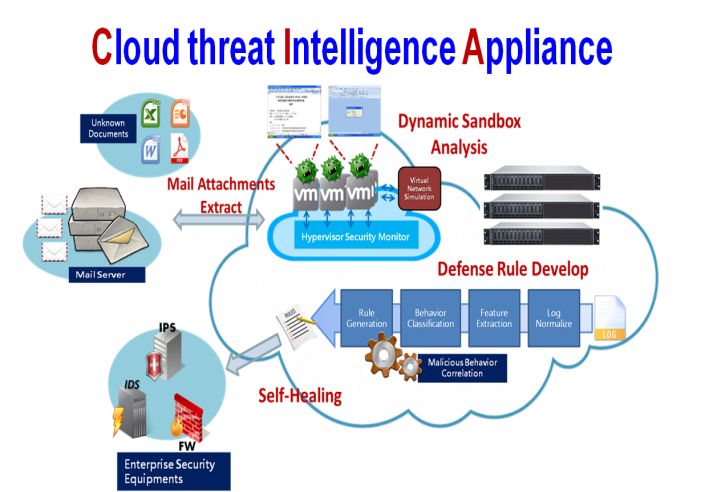
CIA is a Cloud-threat Intelligence Appliance which provides unknown threat analysis service for e-mail attachments. It could efficiently filter out malicious e-mail attachments with 2-tier analysis of static and dynamic characteristics in hypervisor security sandbox. The detection of malicious attachment document file formats includes MS OFFICE 2003/2007/2010 documents (.doc/x、.xls/x、.ppt/x) and Adobe PDF document (.pdf). The analysis of malicious behavior includes network connection (HTTP / HTTPS / MSSQL / MySQL / FTP / SMTP / DNS / SMB), file, registry key operation and process manipulation.
CDS scans for confidential data stored on the endpoint including laptops, desktops, and workstations in order to inventory, secure, or relocate that data. It could scan a corporate website, a file server and the user terminal hosts, to identify Chinese name, telephone number, national ID, account number (bank, credit card) and a variety of sensitive information. The supporting file format includes HTM/HTML, DOC(X), XLS(X), PPT(X), PDF, CSV, TXT, RAR, ZIP, 7Z, PPS, RTF, JSP, ASP, PHP, XML, ODS, ODT, ODP, ODG, and EPUB. With centralized management, enterprises can easily use consistent scan policy and generate integrated statistics reports or csv files for further analyzing. In addition, the system can also help user to deal with the confidential files after completing a scan, such as whether to move, delete or encrypt or to upload them to a specific server for centralized monitor and control.
Industrial Cyber Threat Detector (ICTD)
ICTD is a multi-level deep Intrusion Detection system for industrial control system (ICS). ICTD sniffs packets in transit on the OT network. Through deep packet inspection analysis, ICTD learns to establish normal industrial manufacturing network command behaviors, thus detecting malicious network attack behaviors lurking in the OT environment. The ICTD consists of a 3-level intrusion detection, including ARP Spoofing detection, integrated with Snort detection, and abnormal OT state detection. ICTD analyzes packets through layer 2-7 of the OSI model.
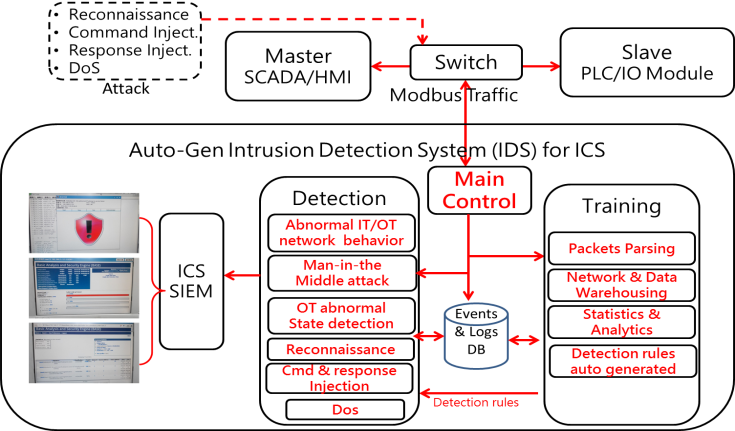
Fig. 1: The flow chart of ICTD: 3-level deep intrusion detection, including ARP Spoofing detection, integrated with Snort detection, and abnormal OT state detection.
ICTD provides key innovative solution in the fellow features:
‧ Anomaly detection rules with automatic learning & automatic deployment rather than time-consuming and labor-intensive manual detection rules
‧ ICTD establishes the whitelist behavior to perform anomaly detection to improve protection by using the blacklist
‧ By using the intelligent method to generate the normal behavior patterns based on correlated operational data, ICTD can resolve the lack of detection capability for industrial network packet attacks lurking in legitimate hosts and devices
‧ Innovative three layer detection and defense mechanism in Industrial network security
III also established the offensive and defense Test bed for industrial control system to verify the ICS security which conforms to the SCADA HMI & PLC architecture and adopts the most common Modbus/TCP industrial standard protocol, provides 7x24 continuous operation for controlling water level in the water treatment system.
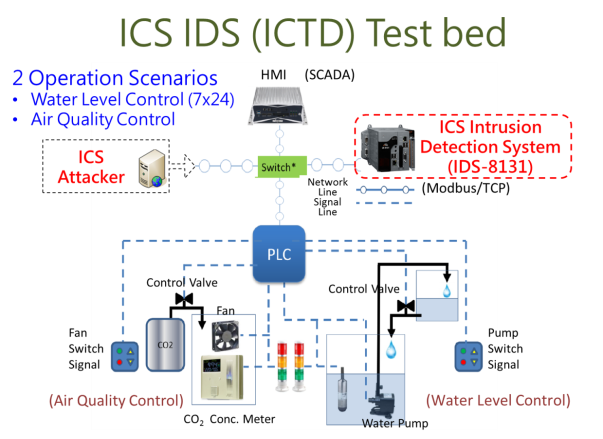
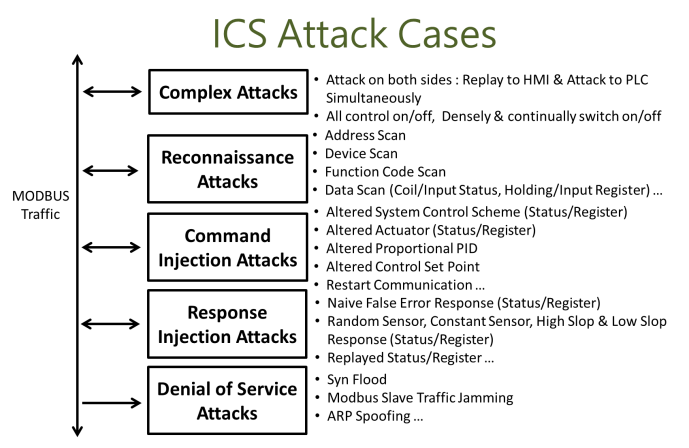
FIG. 3 ICS cybersecurity Test bed & ICS Penetration Test Cases.
Demo Video URL https://youtu.be/meBm_vGjtf4